Now day security threats are everywhere in the web, new security holes are discovered everyday, but sadly there are no instant patches available. If you are a firefox user, this problem is worse, as it lacks the sandbox feature like chromium or Google chrome browser.
Here’s how to protect yourself from such threats by running firefox in sandbox environment with firejail.
Contents
What is firejail ?
Firejail is an extremely lightweight Linux namespace based sandbox application, could be used with both GUI and CLI applications with minimal effort. Firejail could do even more, like traffic shaping, application spacific DNS server and default gateway etc. etc.
It could effectively run most apps with limited permission and system resource to minimize security risk. There's also a GUI app firetools , to launch and monitor apps with firejail.
Installing firejail and firetools
Firejail is already in Debian testing and Ubuntu 15.10 (Wily Werewolf) official repository, there are also binary deb and rpm packages available at sourceforge. Download the relevant binary package from this sourceforge repository and install it with your package manager.
For Debian based systems, use this the apt command to install.
sudo dpkg -i firejail_0.9.30_1_amd64.deb
Now download the relevant firetools package from here and install it. Firetools requires basic Qt4 or Qt5 application runtime libraries, make sure they are installed too.
sudo dpkg -i firetools_0.9.30_1_amd64.deb
Firetools is optional, but it is easy to launch applications and monitor them with firejail.
You could also install firejail in Debian testing and Ubuntu 15.10 straight from the official repository.
sudo apt-get install firejail
Start firefox in snadbox environment with firejail
Now It's the time to run firefox in sandbox environment, first we are going to do this with command line.
firejail firefox
Just this ! Make sure that no other previous firefox instances are running already. In such case use this command
firejail firefox --new-instance
Some advanced firejail sandbox commands
-
- Start Firefox in a seccomp sandbox environment
firejail --seccomp firefox
- Start Firefox in a Linux capabilities sandbox environment
firejail --caps firefox
- Start a Firefox with a new tmpfs private home directory
firejail --private firefox
- List all running sandboxes
firejail --list
- Print a tree of all sandboxed processes
firejail --tree
- Start Firefox in a seccomp sandbox environment
Launching and monitoring sandboxed apps with firetools
Firetools is the GUI app for monitoring and launching other apps in the sandbox environment, just find the Firetools launcher icon and Launch it.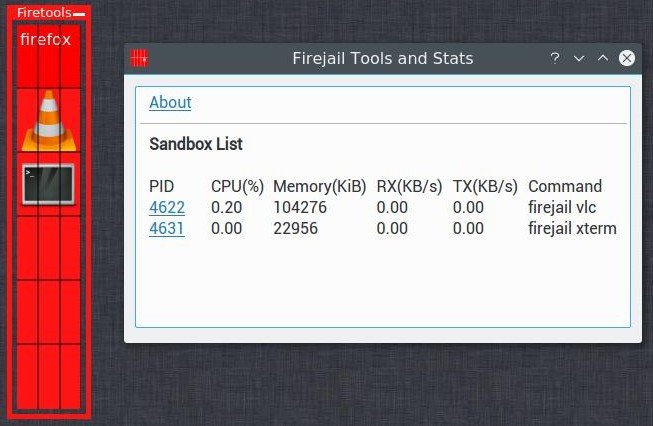
Create a custom sandboxed Firefox app launcher
For easy access and quick launching, you may create a application launcher .desktop file to directly launch firefox in snadboxed environment.
Just create a text file named sandbox-firefox.desktop with your favorite text editor and put the text bellow inside it.
[Desktop Entry] Type=Application Name=Sandboxed Firefox GenericName=Secured Firefox Exec=firejail firefox Categories=Network Icon=firefox Terminal=false
After this move the launcher to a proper location.
sudo mv sandbox-firefox.desktop /usr/share/applications/
sudo update-desktop-database
The Firefox icon may or may not show properly, depending upon your system, but it's fine. Now run secured Firefox from this launcher icon.
Credits: Here is the blog link of filejail original author, the whole thing is explained in much details. So that's it 🙂 If you have any question, please leave a comment and don't forget to share this tip with your friends.
Thank you so much!!
Secomp and caps are part of the default Firefox profile, simply #firejail firefox will start a sandboxes browser session with both these capabilities enabled.
Thanks buddy for your valuable comment, I didn't investigated the firejail profiles under /etc/firejail deeply.
Small type "snadbox" but otherwise useful information. Cheers.
Thanks, Hope you like this.