So, what the heck is WebRTC leak test? If you have no idea about it, read on.
Later in this article we'll have a short discussion about what is WebRTC protocol, how it's leaked, what's the potential risk of WebRTC leak and how to prevent it.
Before that, have a look at this automated service below, it performs a WebRTC leak test.
It tries to detect local IP address through the WebRTC STUN origin header, which you can use to verify whether your browser and VPN service is leaking the local IP address or not.
What is WebRTC ?
Web Real-Time Communication or WebRTC in short, is a protocol to enable real time audio-visual and P2P communication between two or more browsers. The main development goal was to achieve better browser based VoIP and videoconferencing functionality.
Later the project was open sourced by Google, thereafter implemented by various other companies, including Mozilla on their Firefox web browser. Now WebRTC is used by Facebook Messenger, YouTube, Google Hangouts, OpenTok and many more. You can read more here.
WebRTC leak is a type of vulnerability on web browsers which exposes your local IP address through the WebRTC stun origin header.
The STUN protocol is required for seamless WebRTC experience.
If overlooked, it's quite easy to add some JavaScript code on web page and get the local IP, even if you're using a VPN. Once the attacker have the IP address, there're many ways to send it over internet for monitoring and logging purpose.
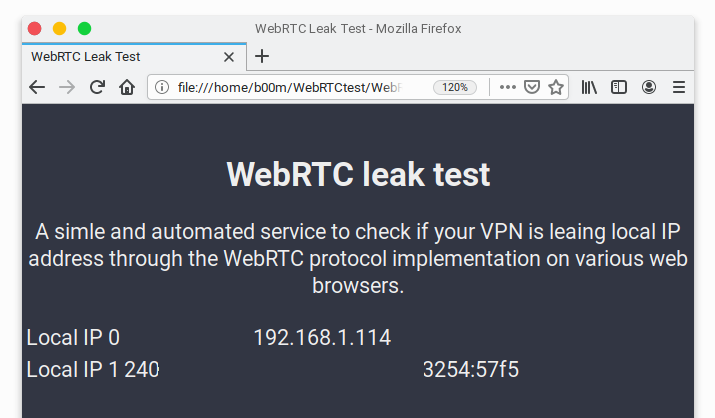
So, it's clear that even if you're using a VPN or Tor or any other anonymity service, your local IP address could be tracked through WebRTC leakage.
The problem is even worse, specially when using IPv6 to connect to the internet.
The reason, IPv6 is designed to provide unique public IP to each device.
Read more about How to disable IPv6 on Windows.
How to prevent WebRTC leak on browsers?
With all the goodness, WebRTC also poses a threat to online privacy and security.
So, WebRTC is no so good for online privacy and you should disable it if there's no use.
On Google Chrome or Chromium browser, the local IP is automatically fuzzed by default. Regardless of desktop OS platforms, either it's Windows, macOS or any Linux distribution.
However, on Firefox, the local IP is exposed through WebRTC, however it could be easily fixed by using plugins like uBlock Origin.
Some less popular bowers on Linux, like Falkon, Midori etc, which uses Either WebKit or WebEngine as rendering engine, are vulnerable to WebRTC leak. Apparently there's no easy way of fixing this issue.
But the real threat is on Android platform. Chrome browser for Android and many more popular browser are vulnerable to WebRTC leak.
Worse, there's no simple way to install plugins/ add-ons on Android to prevent WebRTC leak.
That's when you should be extra cautious if you truly value your online privacy. You can use Firefox beta on Android to install plugins like uBlock Origin.
Leave a Reply